8.3. The Information Security Triad
The previous section highlighted the motivations and impact of cybercrime on Canadian businesses. It is important for companies to invest in tools, and policies to help mitigate the risk of cybercrime. The Information Security Triad or CIA Triad is a model that can be used to help in the development of security policies. It contains three main components: confidentiality, integrity and availability.
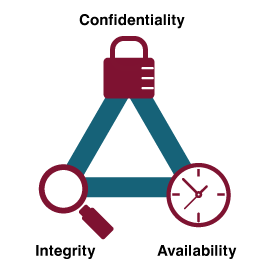
Confidentiality
Protecting information means you want to be able to restrict access to those who are allowed to see it. This is sometimes referred to as NTK, (Need to Know). Everyone else should be disallowed from learning anything about its contents. This is the essence of confidentiality.
Integrity
Integrity is the assurance that the information being accessed has not been altered and truly represents what is intended. Just as a person with integrity means what he or she says and can be trusted to consistently represent the truth, information integrity means information truly represents its intended meaning. Information can lose its integrity through malicious intent, such as when someone who is not authorized makes a change to intentionally misrepresent something. An example of this would be when a hacker is hired to go into the university’s system and change a student’s grade. Integrity can also be lost unintentionally, such as when a computer power surge corrupts a file or someone authorized to make a change accidentally deletes a file or enters incorrect information.
Availability
Information availability is the third part of the CIA triad. Availability means information can be accessed and modified by anyone authorized to do so in an appropriate timeframe. Depending on the type of information, appropriate timeframe can mean different things. For example, a stock trader needs information to be available immediately, while a sales person may be happy to get sales numbers for the day in a report the next morning. Online retailers require their servers to be available twenty-four hours a day, seven days a week. Other companies may not suffer if their web servers are down for a few minutes once in a while.
“Chapter 6: Information Systems Security” from Information Systems for Business and Beyond (2019) by David Bourgeois is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License, except where otherwise noted.

