5.7. Why Databases?
Data is a valuable resource. However, many people are unfamiliar with database software, and therefore use other products, such as spreadsheets, to store and manipulate business data. As a result, the data becomes redundant, inconsistent, inaccurate, and fails to meet the characteristics of valuable information. For a small data set, the use of non-database tools may not cause problems, but can soon become unmanageable and lead to serious errors. There are a number of characteristics that distinguish the database approach from the file-based system or approach. The following are the benefits of using a database approach.
Control of redundant data
Redundant data is data that is repeated in a database, which can cause the data set to be inconsistent. In the database approach, ideally each data item is stored in only one place in the database. In some cases redundancy still exists to improve system performance, but such redundancy is controlled and kept to a minimum. See below for an illustrative example to explain why redundant data are harmful.
Example of Redundant Data
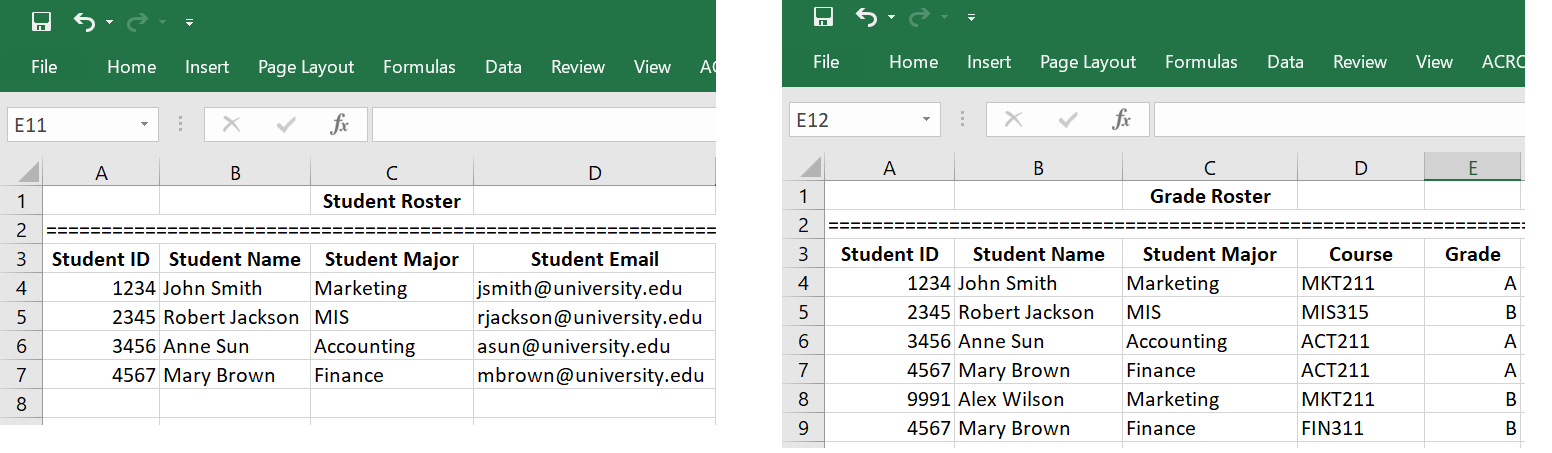
Suppose the registrar’s office has two separate files that store student data: one is the registered student roster which records all students who have registered and paid their tuition, and the other is student grade roster which records all students and their grades.
As you can see from the two spreadsheets, this data management system has redundancies. The student’s name and major are recorded in both lists. Redundant data can make data access convenient, but it can have negative consequences. For example, if Mary Brown changes her name or her major, then this information will need to be updated everywhere it is listed. For small data systems, this may be a simple task. However, when the data system is huge, making changes to all redundant data is difficult if not impossible. As a result of data redundancy, the entire data set can be corrupted.
Data Integrity
Data integrity means consistency among the stored data. We use the above illustrative example to explain the concept of data integrity and how data integrity can be violated if the data system is flawed. You can find that Alex Wilson received a grade in MKT211; however, you can’t find Alex Wilson in the student roster. That is, the two rosters are not consistent. Suppose we have a data integrity control to enforce the rules, say, “no student can receive a grade unless she/he has registered and paid tuition”, then such a violation of data integrity can never happen. Database management systems provide capabilities to define and enforce certain constrains to ensure integrity.
Data Sharing
The integration of the whole data in an organization leads to the ability to produce more information from a given amount of data. When the data is centralized in one database it makes it easier.
Security & Recovery
Database management systems allow for restricting unauthorized access through security features that allow for control of user accounts. Not all users of the system have the same accessing privileges. In addition, users may have different views of the database itself as users may not need to be aware of how and where the data they refer to is stored.
As well, if the computer system fails in the middle of a complex update program, the recovery subsystem is responsible for making sure that the database is restored to the stage it was in before the program started executing.
“Chapter 4: Data and Databases” from Information Systems for Business and Beyond (2019) by David Bourgeois is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License, except where otherwise noted.