8.2. Cybercrime
Cybercrime (also referred to as computer crime) is an illegal activity that is committed with the use of a computer, or where a computer is the object of the crime. With the increase in use of digital technology by Canadians, so too is the prevalence of digital crimes and the impact of those crimes. According to Accenture’s Cost of Cybercrime Survey, Canadian organizations spent $9.25 million on average resolving damage done by cyber attacks (Accenture, 2019). In addition, 21% of Canadian businesses reported that they had been impacted by a cyber security incident in 2019. However, only 12% of businesses impacted by incidents reported them to the police, stating that they could resolve them internally or through a contractor/consultant. Around a third of respondents felt the incidents were too minor to report (Bilodeau, et al., 2019).
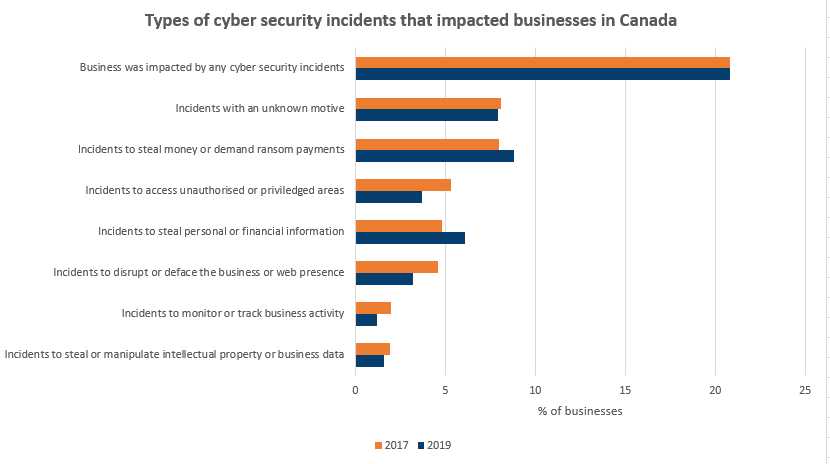
Small and medium enterprises (SME) are most likely to face cyber threat activity that often has immediate financial or privacy implications. Canadian businesses are targeted by cyber threat actors for their data about customers, partners and suppliers, financial information and payment systems, and proprietary information. Motivations for the cybercrimes experienced by Canadian businesses vary as can be seen in the image below but ultimately result in either stealing money from a business or selling personal information for money. Cyber security incidents can also result in reputational damage, productivity loss, intellectual property theft, operational disruptions, and recovery expenses (Canadian Centre for Cyber Security, 2021).
Personal Information Protection
According to Canada’s Personal Information Protection of Electronic Documents Act (PIPEDA) private businesses are required to safeguard personal information collected during commercial activity and report breaches to the privacy commissioner and the individuals impacted. For more information refer to the Office of the Privacy Commission of Canada’s website on privacy breaches (Office of the Privacy Commissioner of Canada, 2018). It is important that businesses understand the requirements concerning collecting and storing personal information and investigate ways to safeguard it to minimize the impacts.
Types of Cybercrime
Cybercrime can be categorized based on whether a network or computer technology is the target of the crime, or where the technology is used to commit a crime. Malware and Denial of Service (“DoS”) or Distributed Denial of Service (“DDoS”) attacks are examples of where the target is the technology.
Technology as Target of Crime
Malware, which is a short form for malicious software, is any program that is designed to steal or destroy data and systems. Some examples of malware include viruses, worms, spyware, and ransomware.
| Viruses and worms | are codes that replicate to destroy data. A virus requires a host in order to spread, such as an executable file, where a worm can spread unaided. |
| Spyware | is software that gathers data, usually personal, about you and sends it without your knowledge. |
| Ransomware | is malware that infects a computer and encrypts the data and requires payment (ransom) of the owner in order to access it again. |
A denial-of-service (DoS) attack does exactly what the term suggests: it prevents a web server from servicing authorized users. Consider the following scenario. Dozens of computers are whirring away at an online bookmaker in the offshore gambling haven of Costa Rica. Suddenly a mass of blank incoming messages floods the company’s computers, slowing operations to a trickle. No legitimate customers can get through to place their bets. A few hours later, the owner gets an e-mail that reads, “If you want your computers to stay up and running through the football season, wire $40,000 to each of 10 numbered bank accounts in Eastern Europe.”
The choice of a gambling site for this example is deliberate. Many companies in the online gambling industry suffer hundreds of such attacks each year (Baker & Grow, 2004). Most gambling operations are willing to pay the ransom and return to business as usual, so denial of service to businesses in this industry has become very lucrative. Online gambling operations are good targets because they’re illegal, and they cannot get help from law-enforcement authorities. However, extortionists have been known to hit other targets, including Microsoft and the Recording Industry Association of America. The problem could become more serious if they start going after e-commerce companies and others that depend on incoming orders to stay afloat.
A DDoS is when multiple computers send requests so that the service crashes.
Technology Used to Commit Crime
Identity theft, social engineering, hacking, phishing, spoofing, and software piracy are all examples of crimes that are facilitated with the aid of computer technology.
Identity theft is when a criminal gains access to your personal information and uses it without your knowledge.
Social engineering is when criminals lure individuals into sending them personal, confidential data that can be used in crime. For example, someone phones you, posing as a customer service representative asking for your banking log-on information.
Hacking is when someone accesses a computer without permission.
Phishing occurs when a user receives an e-mail that looks as if it is from a trusted source, such as their bank or employer. In the e-mail the user is asked to click a link and log in to a website that mimics the genuine website, then enter their ID and password. The userID and password are then captured by the attacker. See an example of a phishing email in the image below.
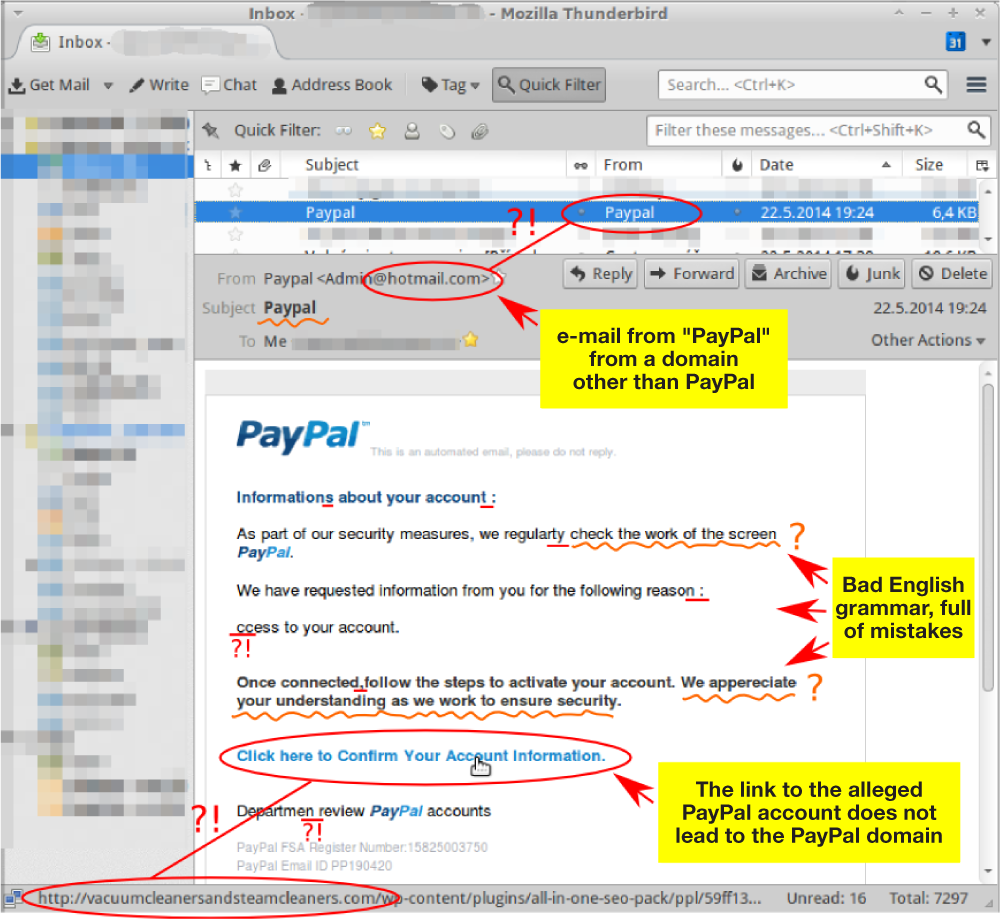
Spoofing is a technique where culprits disguise their identities by modifying the address of the computer from which the scheme has been launched. Typically, the point is to make it look as if an incoming message has originated from an authorized source. Then, once the site’s been accessed, the perpetrator can commit fraud, spy, or destroy data. You could, for example, spoof a manufacturing firm with a false sales order that seems to have come from a legitimate customer. If the spoof goes undetected, the manufacturer will incur the costs of producing and delivering products that were never ordered (and will certainly never be paid for).
Piracy
Another crime that is committed with the use of a computer is software piracy, which is the illegal copying and distribution or use of software. Technology makes it easier to create and sell intellectual property, but it also makes it easier to steal it. Since digital products can be downloaded and copied almost instantly over the Internet, it’s a simple task to make perfect replicas of your favourite copyright-protected songs, movies, TV shows, and computer software, whether for personal use or further distribution. When you steal such materials, you’re cheating the countless musicians, technicians, actors, programmers, and others involved in creating and selling them. Theft cuts into sales and shrinks corporate profits, often by staggering amounts. Online piracy costs between $30 and $71 billion dollars in lost revenue in a year worldwide (Whitten, 2021).
“Online Security” by the Learning Portal is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.

