10.3: Risk Management Strategies to Mitigate the Supply Chain Vulnerability

Risk Management
Here is a clear explanation of risk management adapted from Amulya Gurtu & Jestin Johny’s Supply Chain Risk Management: Literature Review .
Risk management refers to the implementation of strategies and plans to manage supply chain networks through constant risk assessment. It reduces vulnerabilities to ensure resilience in supply chains. Not all supply chains have the same risks, but some risks are common. The risks are also specific to an area of business or the field of study. A supply chain is as strong as the most vulnerable member of the supply chain. Therefore, the longer a supply chain, the greater the risk of failure of the supply chain. Supply chains have many players. A high number of players present risks. However, building a robust supply chain is expensive. Numerous research articles have suggested the need for robust supply chains due to the extent of the adverse effects of risk on a company’s performance. A risk event is an indicator of a threat that disrupts a supply chain. Global supply chains have many challenges and greater risks. The dependence on an organization for parts has changed to a supply chain. This requires greater transparency and sharing of information among supply chain players.
“Risk management refers to strategies, methods, and supporting tools to identify and control risk to an acceptable level” (Alhawari et al. 2012). Risk management can also be referred to as a synchronized set of actions and approaches to direct an organization to minimize the risk for achieving organizational goals. Managing risks allows the decision-maker to understand and assess the impact of risk in a supply chain network. Controlling complexity leads to higher cost efficiency and reduces risks.
Risk detection plays a pivotal role before disruption occurs. Force majeure disruptions are challenging to manage but can be estimated through conscious risk assessment strategies, identifying risk indicators, and applying the principles of Total Quality Management (TQM) in sharing information among SCM partners. Corporations should have contingency plans in case of a disruptive event. Performance failures of a supply chain can be monitored through audits in an organization. Toyota has applied these principles in its supply chains and minimized the disruptions due to product recalls.
Strategies to control risk may be divided into seven categories: prevention, rescheduling, conjecture, numerical and economic, vertical integration, risk-sharing, and technology and security.
- The prevention strategy is used when risks are linked with each product or its terrestrial markets or when close engagement with suppliers/customers is not possible. Divestiture of resources, delay of entry, or contributing to less ambiguous markets are examples of prevention strategies.
- Flexibility and delay in spending are rescheduling strategies. Market demand, customization of products or services, input costs, product life cycle, and product modularity affect rescheduling.
- Conjecture is the opposite of rescheduling, and decisions are made on the basis of projected or anticipated demand. Supply chain resources are leveraged to maximize competitive advantage.
- Financial risks are addressed through numerical and economic approaches. The numerical approach is for a large population, e.g., insurance. The occurrence of an event for many people at the same time requires an economic approach.
- Some risks incentivize vertical integration, which reduces risks through better supply and demand control. Examples of such incentives include opportunism and asset specificity, capacity constraints, and improved supplier–buyer power balance. Contracts with flexibility for possible changes due to environmental constraints reduce risks. Designing flexible contracts acts as a control mechanism.
- Outsourcing or offshoring transfers SCM risks and helps to share such risks with suppliers.
- Technology helps to detect nuclear, chemical, or biological hazards and reduces the risk of carrying such shipments.
Practical Procurement: Scenarios and Solutions
Remi Sanchez, the newly appointed Chief Procurement Officer at MetroCity Public Transport Authority (MPTA), faces a significant challenge. MPTA procures essential components for the city’s extensive public transportation network, including buses, trains, and maintenance equipment. Remi recently discovered that several key suppliers are experiencing delivery delays due to geopolitical tensions, disrupting the supply chain. This problem is critical for Remi because any delay in procurement could lead to service interruptions, affecting thousands of daily commuters and tarnishing MPTA’s reputation.
MPTA, a government agency with over 2,000 employees, manages the public transportation system for MetroCity, serving a population of over 5 million residents. The agency’s primary revenue is ticket sales, government subsidies, and advertising. MPTA’s operations depend heavily on a reliable supply chain to maintain and upgrade its fleet of vehicles and infrastructure. The agency works with various suppliers, from local manufacturers to international corporations, making it vulnerable to various risks, including political instability, natural disasters, and economic fluctuations.
Remi has several options to address the supply chain vulnerabilities. The first option is to diversify the supplier base by identifying and contracting with additional suppliers from different geographical regions, including more local suppliers. This strategy could reduce dependency on any single supplier and mitigate the risk of disruptions. However, it may increase procurement costs and require additional resources for supplier management.
The second option is to implement a robust risk assessment and monitoring system. Remi can identify potential risks early and develop contingency plans using advanced analytics and real-time data. This approach aligns with Total Quality Management (TQM) principles and emphasizes continuous improvement and proactive risk management. While this option could enhance MPTA’s resilience, it requires significant investment in technology and training.
The third option is to establish strategic partnerships with key suppliers. MPTA can improve transparency and collaboration within the supply chain by fostering closer relationships and sharing information. This strategy involves negotiating long-term contracts with suppliers, which could provide stability and predictability. However, it may limit MPTA’s flexibility to switch suppliers in response to changing market conditions.
Remi must decide which strategy to pursue to ensure the resilience of MPTA’s supply chain. The decision is urgent because any further delays could lead to severe service disruptions, impacting the city’s economy and the daily lives of its residents.
Discussion Questions
- What are the potential benefits and drawbacks of diversifying MPTA’s supplier base? How can this strategy mitigate supply chain risks?
- How can implementing a risk assessment and monitoring system enhance MPTA’s supply chain resilience? What are the key components of such a system?
- In what ways can strategic partnerships with key suppliers improve supply chain transparency and collaboration? What are the potential risks associated with this approach?
Source: Scenario and questions created with the assistance of Microsoft Copilot.
Effective Risk Management Processes
Risk Management Framework
As discussed earlier, a defined risk management framework (RMF) outlines the strategic decision-making and management of the effect of uncertainty on the possibility of an organization achieving its objectives.
A risk management framework provides a structure for the management of risk. Further it ensures that the risk management process is integrated into the overall business and governance strategy of an organization.
The risk management cycle is part of the risk management framework and outlines the steps needed to manage risks.
Risk Management Cycle
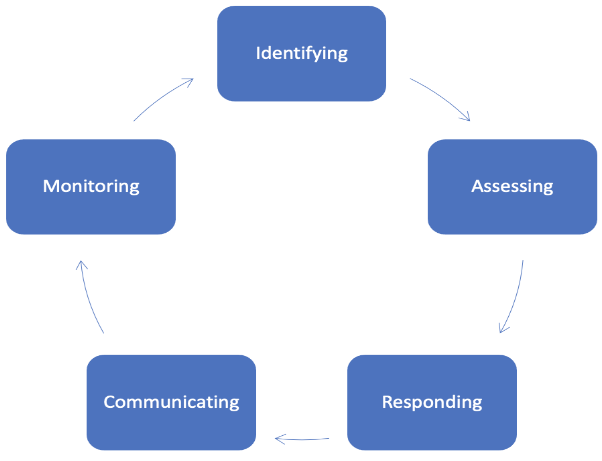
Companies need to use an effective risk management process that consists of the following steps: identifying, assessing, responding, communicating, and monitoring risks in the global value chain. The process is the so-called risk management cycle. The risk management cycle is a tool for helping companies in various industries recognize potential risks and then manage risks at all levels. The most comprehensive risk management cycle was created by the Government of Canada (2016). The risk management cycle helps organizations to choose “the best course of action under uncertainty” (Government of Canada, 2016). The cycle includes the following steps: identify, assess, respond, communicate, and monitor risks (Government of Canada (2016). It is a systematic, proactive, and ongoing process that equips organizations to be more effective, high-performers, and build confidence when companies face uncertainty (Government of Canada, 2016).
Identifying Risk
Identifying risk in the global value chain is the initial step in the risk management process. In this step, the organization has to identify as many risks as possible and share them with every stakeholder and third party. Next, identify warning signs of risks by creating questions, for example, is our new technology proven and mature for the global value chain? Why does the organization have significant gaps between partners and information? Why does the organization not have a mitigation or contingency plan? (FITT, 2021)
The organization should share the mitigation plan, expectations, and tools with stakeholders, partners, and staff. According to the Government of Canada (2016), there are several techniques and tools available for identifying risks, such as checklists, workshops, and risk assessment forms (Government of Canada (2016). In addition, identification activities have to be provided by the staff, such as identifying people who should be involved in identifying risk roles, documenting identified risks, and determining what type of information should be collected and recorded (Government of Canada, 2016).
Assessing Risk
Assessing risk includes analyzing and prioritizing steps (Government of Canada, 2016). The scope of the risk has to be determined by the assigned person. Also, determine the factors about the severity of this risk and how this risk has affected businesses in the past. The likelihood and the impact of an event are the significant parts of this step. The organization should take into account both impact and probability. Probability is how often the event has occurred in the past. For assessing risks, companies should characterize, evaluate, and prioritize risks to support the chosen decision. This action will help the organization to manage risk in the future. There are a variety of assessments that can help assess risk: qualitative, quantitative, and semi-quantitative.
- Quantitative assessment consists of numerical risk criteria such as numbers which can be counted or measured.
- Qualitative assessment is based on the qualitative descriptions of risks, such as characteristics or information that cannot be counted.
- Semi-quantitative assessment combines quantitative and qualitative data.
After getting information, risks have to be measured and ranked. The top priority risks have the highest probability and greatest impacts (FITT, 2021). There are some specially designed tables for the purpose of assessing risk.
Responding to Risk
According to the Government of Canada (2016), this step includes selecting and implementing measures to counter the risk. Several mitigation strategies can be used when responding to the threat: accepting, reducing, avoiding, monitoring, and transferring risks (Government of Canada, 2016).
- Accepting risk is the same as risk retention, and an organization accepts a particular risk because it is not worth spending money to mitigate it. Acceptance is the most common approach for smaller risks in the global value chain.
- Risks can be reduced through control or prevention. Installing security systems, burglar alarms, and protective equipment are common approaches to minimizing risks.
- The avoidance strategy applies to organizations that want to eliminate as many challenges and potential risk sources as possible. This strategy is not acceptable for all hazards and can be mitigated by creating policies, procedures, training etc. For example, if a country is politically unstable, the company can avoid the political risk by not expanding to that country.
- Monitoring risks is an ongoing process within the global value chain.
- Companies can transfer risks to an insurance company by purchasing an insurance policy. Also, risk may be transferred to a third party, who will be responsible for consequences and losses.
Communicating Risk
The Government of Canada (2016) describes this step as the risk management process of communicating and reporting information about risks to a particular department. The communication process must be internally between employees and externally between clients, stakeholders, and third parties. An integral part of communication is providing enough information to make the right decision (Government of Canada, 2016).
Monitoring Risk
Regular review of risk information and mitigation plans is an ongoing process for the global value chain. Reviewing risk responses to ensure that the plan is implemented effectively and efficiently is an essential part of the cycle because it helps to identify and execute improvements or new opportunities. (Government of Canada, 2016).
Exhibit 10.3 provides a visual representation of the Risk Management Cycle.
We will now review some of the steps in the risk management cycle in greater detail.
Risk Evaluation or Assessment
After the potential risks have been identified, the project team evaluates each risk based on the probability that a risk event will occur and the potential loss associated with the risk. Not all risks are equal. Some risk events are more likely to happen than others, and the cost of a risk can vary greatly. Evaluating risks for the probability of occurrence and the severity of impact or the potential loss to the project is the next step in the risk management process.
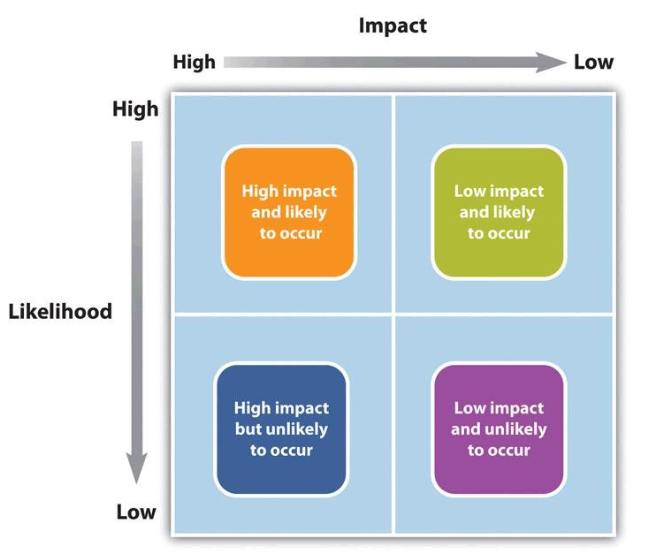
Having criteria to determine high-impact risks can help narrow the focus on a few critical risks that require mitigation. For example, suppose high-impact risks are those that could increase the project costs by 5% of the budget. Only a few potential risk events meet these criteria. These are the critical few potential risk events that the project management team should focus on when developing a project risk mitigation or management plan. Risk evaluation is about developing an understanding of which potential risks have the greatest possibility of occurring and can have the greatest negative impact on the project (see Exhibit 10.4). These become the critical few risk events that need to be planned for.
There is a positive correlation between project risk and project complexity, i.e., both increase or decrease together. A project with new and emerging technology will have a high-complexity rating and a correspondingly high risk. The project management team will assign the appropriate resources to the technology managers to ensure the accomplishment of project goals. The more complex the technology, the more resources the technology manager typically needs to meet project goals, and each of those resources could face unexpected problems.
Risk evaluation often occurs in a workshop setting. Building on the identification of the risks, each risk event is analyzed to determine the likelihood of occurrence and the potential cost if it did occur. The likelihood and impact are rated high, medium, or low. A risk mitigation plan addresses items that are rated high on both likelihood and impact.
Example: Risk Analysis of Equipment Delivery
A project team analyzed the risk of some important equipment not arriving on time for the project. The team identified three pieces of equipment that were critical to the project and would significantly increase costs if they arrived late. One of the vendors, who was selected to deliver an important piece of equipment, had a history of being late on other projects. The vendor was good and often took on more work than it could deliver on time. This risk event (the identified equipment arriving late) was rated as having a high likelihood of occurring with a corresponding high impact on the project. The other two pieces of equipment had potentially a high impact on the project but had a low probability of occurring.
Not all project managers conduct a formal risk assessment on a project. One reason, as found by David Parker and Alison Mobey in their phenomenological study of project managers, was a low understanding of the tools and benefits of a structured analysis of project risks (2004). The lack of formal risk management tools was also seen as a barrier to implementing a risk management program. The project manager’s personality and management style also play into risk preparation levels. Some project managers are more proactive and develop elaborate risk management programs for their projects. Other managers are reactive and are more confident in their ability to handle unexpected events when they occur. Yet others are risk averse and prefer to be optimistic and not consider risks or avoid taking risks whenever possible.
On projects with a low-complexity profile, the project manager may informally track items considered risk items. On more complex projects, the project management team may develop a list of items perceived as higher risk and track them during project reviews. On projects of even greater complexity, the process for evaluating risk is more formal, with a risk assessment meeting or series of meetings during the life of the project to assess risks at different phases of the project. On highly complex projects, an outside expert may be included in the risk assessment process, and the risk assessment plan may take a more prominent place in the project implementation plan.
On complex projects, statistical models are sometimes used to evaluate risk because there are too many different possible combinations of risks to calculate them one at a time. One example of the statistical model used on projects is the Monte Carlo simulation, which simulates a possible range of outcomes by trying many different combinations of risks based on their likelihood. The output from a Monte Carlo simulation provides the project team with the probability of an event occurring within a range and for combinations of events. For example, the typical output from a Monte Carlo simulation may indicate a 10% chance that one of the three important pieces of equipment will be late and that the weather will also be unusually bad after the equipment arrives.
Risk Mitigation
After the risk has been identified and evaluated, the project team develops a risk mitigation plan, which is a plan to reduce the impact of an unexpected event. The project team mitigates risks in various ways:
- Risk avoidance
- Risk sharing
- Risk reduction
- Risk transfer
Each of these mitigation techniques can be an effective tool in reducing individual risks and the risk profile of the project. The risk mitigation plan captures the risk mitigation approach for each identified risk event and the actions the project management team will take to reduce or eliminate the risk.
Risk avoidance usually involves developing an alternative strategy that has a higher probability of success but usually at a higher cost associated with accomplishing a project task. A common risk avoidance technique is to use proven and existing technologies rather than adopt new techniques, even though the new techniques may show promise of better performance or lower costs. A project team may choose a vendor with a proven track record over a new vendor that is providing significant price incentives to avoid the risk of working with a new vendor. The project team that requires drug testing for team members is practising risk avoidance by avoiding damage done by someone under the influence of drugs.
Risk sharing involves partnering with others to share responsibility for risky activities. Many organizations that work on international projects will reduce political, legal, labour, and other risk types associated with international projects by developing a joint venture with a company located in that country. Partnering with another company to share the risk associated with a portion of the project is advantageous when the other company has the expertise and experience the project team does not have. If a risk event does occur, then the partnering company absorbs some or all of the negative impact of the event. The company will also derive some of the profit or benefit gained by a successful project.
Risk reduction is an investment of funds to reduce the risk associated with a project. For international projects, companies will often purchase a currency rate guarantee to reduce the risk associated with fluctuations in the currency exchange rate. A project manager may hire an expert to review a project’s technical plans or cost estimates to increase confidence in that plan and reduce the project risk. Assigning highly skilled project personnel to manage high-risk activities is another risk-reduction method. Experts managing a high-risk activity can often predict problems and find solutions that prevent the activities from having a negative impact on the project. Some companies reduce risk by forbidding key executives or technology experts to travel on the same airplane.
Risk transfer is a risk reduction method that shifts the risk from the project to another party. The purchase of insurance on certain items is a risk-transfer method. The risk is transferred from the project to the insurance company. A construction project in the Caribbean may purchase hurricane insurance that would cover the cost of a hurricane damaging the construction site. The purchase of insurance is usually in areas outside the control of the project team. Weather, political unrest, and labour strikes are examples of events that can significantly impact the project and that are outside the control of the project team.
Contingency Plan
The project risk plan balances the cost of implementing mitigating measures against the benefit to the project. The project team often develops an alternative method for accomplishing a project goal when a risk event has been identified that may frustrate the accomplishment of that goal. These plans are called contingency plans. The risk of a truck drivers’ strike may be mitigated with a contingency plan that uses a train to transport the needed equipment for the project. If a critical piece of equipment is late, the impact on the schedule can be mitigated by changing the schedule to accommodate a late equipment delivery.
Contingency funds are funds set aside by the project team to address unforeseen events that cause the project costs to increase. Projects with a high-risk profile will typically have a large contingency budget. Although the amount of contingency allocated in the project budget is a function of the risks identified in the risk analysis process, contingency is typically managed as one line item in the project budget.
Some project managers allocate the contingency budget to the items in the budget with high risk rather than developing one line item for contingencies. This approach allows the project team to track contingency expenses against the risk plan. This approach also allocates the responsibility to manage the risk budget to the managers responsible for those line items. The availability of contingency funds in the line item budget may also increase the use of contingency funds to solve problems rather than finding alternative, less costly solutions. Most project managers, especially on more complex projects, manage contingency funds at the project level, with the approval of the project manager required before contingency funds can be used.
Public Procurement Playbook
Watch this video to learn more about risk management.
Source: Skill Dynamics. (2012, Sep 14.) Risk Management: The Method – Procurement Training – Purchasing Skills. Video. YouTube. https://youtu.be/baI_exaDjiI?si=115F0uzNxZpP3xtQ
Checkpoint 10.3
Image Description
Exhibit 10.3: The image depicts a risk management cycle consisting of five stages arranged in a circular flow, indicating a continuous process. Each stage is represented by a rounded rectangle with text inside, connected by arrows showing the cycle’s direction. Starting from the top, the stages are as follows: “Identifying” is at the top center, followed by “Assessing” to the right. Below “Assessing” is “Responding,” and to the left of it is “Communicating.” Finally, “Monitoring” is located in the top left, completing the cycle back to “Identifying.” The arrows indicate a clockwise motion, emphasizing the iterative nature of the process.
[back]
Exhibit 10.4: The image depicts a risk assessment matrix designed to categorize risks based on their impact and likelihood. The matrix is composed of four quadrants within a square grid, each representing a different risk priority level. The horizontal axis is labeled “Impact,” increasing from left (High) to right (Low). The vertical axis is labeled “Likelihood,” decreasing from top (High) to bottom (Low).
In the top-left quadrant, an orange square represents high impact and likely to occur risks. The top-right quadrant is green, indicating low impact yet likely to occur risks. The bottom-left quadrant is blue, symbolizing high impact but unlikely risks, while the bottom-right quadrant is purple, for low impact and unlikely risks.
[back]
Attributions
“10.3: Risk Management Strategies to Mitigate the Supply Chain Vulnerability” is remixed and adapted from the following:
“Section 7.4: Risk Management Strategies to Mitigate the Supply Chain Vulnerability” from Global Value Chain, copyright © 2022 by Dr. Kiranjot Kaur and Iuliia Kau, licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License, except where otherwise noted.
“Chapter 16: Risk Management Planning” by Adrienne Watt; David Wiley, Project Management Open Resources; and TAP-a-PM in Project Management, Second Edition, copyright © 2014 by Adrienne Watt, licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License, except where otherwise noted.
Exhibit 10.3 is taken from Figure 7.4 in “Section 7.4: Risk Management Strategies to Mitigate the Supply Chain Vulnerability” from Global Value Chain, copyright © 2022 by Dr. Kiranjot Kaur and Iuliia Kau, licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License, except where otherwise noted.
Exhibit 10.4 is taken from “Chapter 16: Risk Management Planning” by Adrienne Watt; David Wiley, Project Management Open Resources; and TAP-a-PM in Project Management, Second Edition, copyright © 2014 by Adrienne Watt, licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License, except where otherwise noted.
“Practical Procurement: Scenarios and Solutions” box was created with the assistance of Microsoft Copilot and is shared under the Creative Commons – CC0 1.0 Universal License.
The multiple choice questions in the Checkpoint boxes were created using the output from the Arizona State University Question Generator tool and are shared under the Creative Commons – CC0 1.0 Universal License.
Image descriptions and alt text for the exhibits were created using the Arizona State University Image Accessibility Creator and are shared under the Creative Commons – CC0 1.0 Universal License.
An entity’s management system designed to (a) identify, understand, and assess potential risks and opportunities (and their interdependence) that may affect the entity, and (b) manage those risks and opportunities to be within its risk appetite, so as to provide proper disclosure and reasonable assurance regarding the achievement of entity objectives.
A strategy that involves the eradication of hazardous activities that can negatively impact an organization or its holdings. This strategy has a higher probability of success but usually comes at a higher cost.
Partnering with others to share responsibility for risky activities.
Measures to reduce the risk associated with a project often through the investment of funds or allocation of risky tasks to highly trained personnel.
Risk reduction method that shifts the risk from the project to another party.

