Section 2 – Responsibilities and Resources in Research Partnerships
Data safety: assess risk and avoid breaches
Oishee Ghosh and Laurence Horton
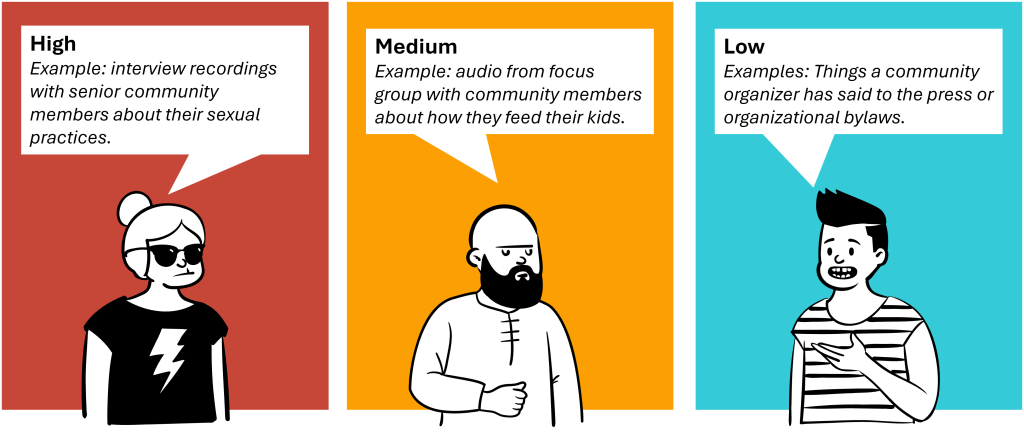
Data risk levels: assessing data safety
With cybersecurity incidents on the rise, data need to be kept safe. Keeping data “safe” is not just one action, but a set of actions, based on different considerations of risk at different moments in time.
These risks are calculated around the nature of data itself: is it sensitive, for example? But also, what can make data unsafe? This could be an accidental loss. Some hypothetical examples of unintentional data loss or accidental breach include sending the wrong attachment on an email, having the bag containing your laptop stolen or left behind somewhere, or where someone is able to read what’s on your screen while you are working in a coffee shop. or it could be things like phishing, ransomware, or hacking, or anything in between.
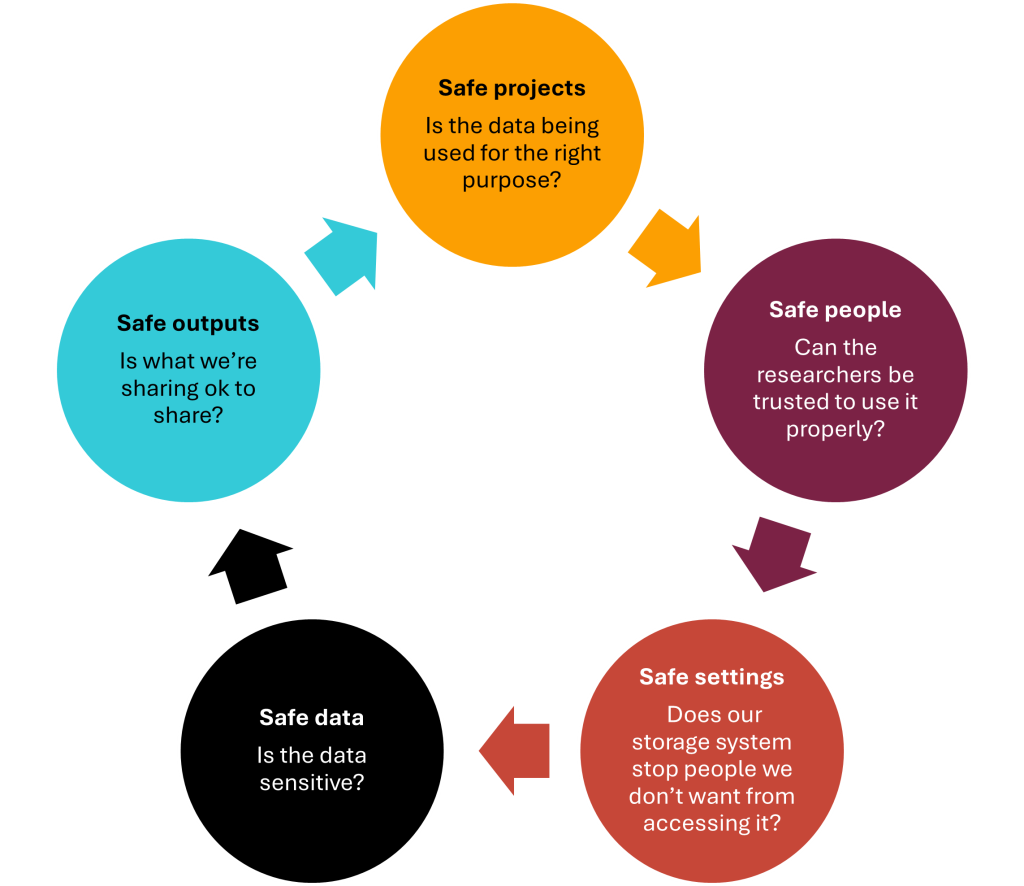
The “Five safes” approach [1] to confidential data asks data managers to think about safety in terms of managerial and data questions.
If information is medium- or high-risk, it may be restricted: open to certain groups, but not to everyone for any purpose. The type of data that can be considered restricted is not as sensitive as confidential data but could still cause harm if there is unauthorized access or it is compromised or lost. This might include personal data, like names, emails, photos, or other data points that on their own might not be disclosive, but in combination can identify individuals. Alternatively, it could be data that is obtained under a subscription or license agreement that prohibits sharing with third parties.
Medium and high risk data require access controls, like some form of authentication in passwords or approved user accounts for restricted data. A sensible approach is to treat all data as restricted until it is decided to do so would be too restrictive or too permissive.
Low-risk data is considered public information. This is data that was collected anonymously and doesn’t contain any personal details. This is the most open category. Provided you have the right to share it, it can be shared with minimal restrictions or requirements. You might still require restricted access rights permissions to modify the data, but people can access copies for their own use with minimal obstacles.
Keeping data safe involves multiple actions to address various risks, including accidental loss, unauthorized access, and cyber threats, with the “Five safes” approach guiding data managers on how to handle distinct types of data securely.
Nuts and bolts: how do we keep data secure?
Data security refers to the practice of protecting digital information from unauthorized access, corruption, or theft throughout its lifecycle. To ensure data stays protected, we can implement a range of measures that ensure the confidentiality, integrity, and availability of data. Effective data security practices can help prevent data breaches, financial losses, and damage to an organization’s reputation. This is crucial for all types of organizations, including academic institutions conducting research and community organizations handling personal data.
Canadian Centre for Cyber Security
The Canadian Centre for Cyber Security provides guidance information on Data Security for:
 Small Org: Smaller organizations might conduct regular security audits, provide employee training on data security, and establish clear policies and procedures for handling sensitive information. Regular backups and implementing access controls for sensitive data are also crucial. With a tiny team, IT provision might be outsourced to an external company. The outsourced IT professional can help guide security practices but should be on board about how to treat research data as opposed to administrative data.
Small Org: Smaller organizations might conduct regular security audits, provide employee training on data security, and establish clear policies and procedures for handling sensitive information. Regular backups and implementing access controls for sensitive data are also crucial. With a tiny team, IT provision might be outsourced to an external company. The outsourced IT professional can help guide security practices but should be on board about how to treat research data as opposed to administrative data.
 Large Org: Larger organizations can set up some systems that the organization could follow if they are holding data themselves long-term, or make sure employees can access data if it is being held by a data repository. Comprehensive security systems, including regular security audits and robust employee training programs assist in data security and maintenance. Detailed data security policies and organization-wide password management solutions are essential. Regular backups with both on-site and off-site storage, along with stringent access controls for sensitive data are essential. An on-staff IT person can oversee backups and security measures as well.
Large Org: Larger organizations can set up some systems that the organization could follow if they are holding data themselves long-term, or make sure employees can access data if it is being held by a data repository. Comprehensive security systems, including regular security audits and robust employee training programs assist in data security and maintenance. Detailed data security policies and organization-wide password management solutions are essential. Regular backups with both on-site and off-site storage, along with stringent access controls for sensitive data are essential. An on-staff IT person can oversee backups and security measures as well.
 No Org: Individuals may need to work with a university or a sponsoring community organization to store and protect research data. However, community members working with a research team might implement personal security measures including using a password manager, enabling protections in software they use for research, and taking cyber security training.
No Org: Individuals may need to work with a university or a sponsoring community organization to store and protect research data. However, community members working with a research team might implement personal security measures including using a password manager, enabling protections in software they use for research, and taking cyber security training.
Common threats and risks
There are many common threats and risks to data security that both individuals and organizations should be aware of. These include malware, phishing, ransomware, and insider threats.
Specifically:
- Malware can infect systems and steal or corrupt data
- Phishing involves hackers tricking individuals into revealing sensitive information
- Ransomware involves locking down your data and demanding payment for its release
- Insider threats in which employees or other trusted individuals misuse their access to data
Understanding these threats is the first step in developing effective strategies to mitigate them. More on common threats and risks on the McMaster RDM Website, Cyber Security.
Top 5 security tips for team members and individuals
- Use complex unique passwords. Using unique, complex passwords for each service helps to prevent unauthorized access. A strong password typically includes a combination of letters, numbers, and special characters. Avoid using information that is easy to guess, such as birthdays or familiar words. Using the same password across multiple services increases the risk of a security breach if one password is compromised. We think this is intuitive but there is evidence that almost 1 in 10 people use the same 4-digit pin.
- Store them in a password manager instead of a spreadsheet. Avoid using unsecured documents such as Microsoft Word or a Google Spreadsheet to store passwords, as unauthorized individuals can easily access these files. Instead, use a password manager as it can securely store and manage passwords. It can also generate and autofill passwords as needed. This is particularly useful for smaller organizations who may not have dedicated IT staff.
- Bitwarden is a dependable password manager with free plans for individuals and paid group plans. Vaultwarden, a self-hosted open-source variant of Bitwarden, can be set up on personal infrastructure. Vaultwarden does require a non-trivial amount of technical expertise and ongoing updates to keep secure and may be best handled by an IT person or System Administrator.
- Enable Multi-Factor Authentication (MFA) where possible. Implementing Multi-Factor Authentication (MFA) adds an essential layer of security due to at least two forms of verification required before granting access. This usually involves inputting your password, and confirmation from a smartphone/secondary device, or biometric verification (i.e. identification by your face or fingerprint). MFA significantly reduces the risk of unauthorized access, even if a password is compromised. This practice is crucial across all sectors, including sensitive research data as well as personal and financial information that organizations might collect. Government of Canada Cyber Security MFA Guidance.
- Learn to recognize phishing attempts. Be cautious of emails or messages that ask for personal information, contain urgent or threatening messages, or have suspicious links or attachments. Always verify the sender’s identity before responding or clicking on any links. Can you recognize an attack? Test yourself with this phishing quiz from Google.
- Update software and hardware regularly. Maintain updates for your software and hardware regularly as it is crucial for maintaining security. Updates often fix weaknesses and improve security features. Automating these updates further mitigates security risks.
NOTE: Always use encryption with sensitive data. Encrypting sensitive data assists in protecting information from unauthorized access. By encrypting data, it is scrambled into a coded format that can only be unscrambled if you have the correct password to unlock it. This means that even if the data is intercepted, it cannot be understood because the hacker doesn’t have the key. Encryption is particularly important for protecting research data, personal information, and financial records. How to Implement Encryption to Protect your Research Data Online has a walkthrough of how to use encryption in Microsoft and VeraCrypt.
Top 3 security tips for organizations
Best practices for community organizations and non-profits include conducting regular security audits, providing employee training on data security, and establishing clear policies and procedures for handling sensitive information. Using resources designed specifically for small organizations can improve data security measures and ensure compliance with relevant regulations.
- Conduct quarterly security audits and provide annual data security training for all staff. This helps in identifying vulnerabilities and educating employees in best practices. Here’s a sample checklist for a Security Audit:
- Physical Security: Check locks on doors and windows, verify access control systems (e.g. keys and key cards), ensure security cameras are operational
- Network Security: Review firewall configurations, check for updated antivirus and anti-malware software, verify secure Wi-Fi settings
- Data Security: Ensure data encryption is in place for sensitive information, verify backup procedures and test data restoration, check access controls for data storage systems
- User Access Controls: Review user accounts and permissions, ensure strong password policies are enforced, check for inactive or outdated user accounts and remove them
- Software Security: Verify that all software is up to date with the latest patches, check for unauthorized or outdated software, ensure secure coding practices are followed for in-house applications
- Incident Response: Review incident response plan and procedures, ensure staff are trained on how to respond to security incidents, test incident response plan with simulated scenarios
- Compliance: Verify compliance with relevant regulations and standards, ensure documentation is up-to-date and accessible, conduct regular compliance audits
- Employee Training: Check records of security training sessions, ensure all employees have completed required training, provide ongoing education on new security threats and best practices – the Government of Canada’s Get Cyber Safe is a great resource for staff training!
- Monitoring and Logging: Verify that logging and monitoring systems are in place, ensure logs are regularly reviewed and analyzed, check for any unusual or suspicious activity
- Third-Party Security: Review security policies of third-party vendors, ensure contracts include security requirements, conduct regular assessments of third-party security practices
- Maintain regular backups of data. Backing up data means it can be restored if you lose data or it gets corrupted. This involves scheduling regular backups (e.g. daily, weekly, monthly) depending on the organization’s needs. Both on-site and off-site storage options should be used to account for multiple cases of data access and loss. The use of reliable backup software, encryption, and access software to create copies and store all critical data is another method of preserving this data. Regular testing and revision of backup procedures on a periodic basis, including the incorporation of recent technologies, will ensure that this system is maintained over time and as the organizational needs change. If an organization has a dedicated IT support person, this can be implemented into their workload. Learn more about strategies for data storage and backup.
- Ensure sensitive data is only accessible by authorized individuals. To protect organizational data, ensure that sensitive data is only accessible to authorized individuals and that access controls are implemented at scale to your data and personnel. Implementing clear policies and training for data handling procedures can support data security best practices. A good rule is the “principle of least privilege”: that staff should only be given permission to information they need to do their job.
- Ritchie, F. (2017). The 'Five Safes': a framework for planning, designing and evaluating data access solutions. Data for Policy 2017: Government by Algorithm? (Data for Policy), London. Zenodo. https://doi.org/10.5281/zenodo.897821 ↵
Is keeping data safe. This can include making sure only the people you want can change it or making sure nobody steals it. It can also be activities like making sure the files still work over time (NIH, n.d.-b)

